Boomi Cloud API Management Developer Blog
RSS FeedAdvisories CVE-2014-6271 and CVE-2014-7169 for GNU Bash
A security advisory was released on 09/24/2014 related to a vulnerability, now informally being referred to as Shellshock, that exists in GNU Bash. For more information about this vulnerability, please refer to CVE-2014-6271 and CVE-2014-7169. An incident response is in effect and immediate actions have been taken by TIBCO Mashery to address this vulnerability. We will update you with more information as it becomes available. Please contact support@mashery.com with questions or concerns.
Mashery understands the impact and is working towards building and deploying the patch for Mashery Local 2.2 customers by end of next week. Also Mashery Local is less vulnerable as it sits behind the firewall.
More on CORS
We added a bunch of important improvements to Mashery Traffic Manager recently that really rounds off our support for a very important industry standard CORS. Hope you find them useful !
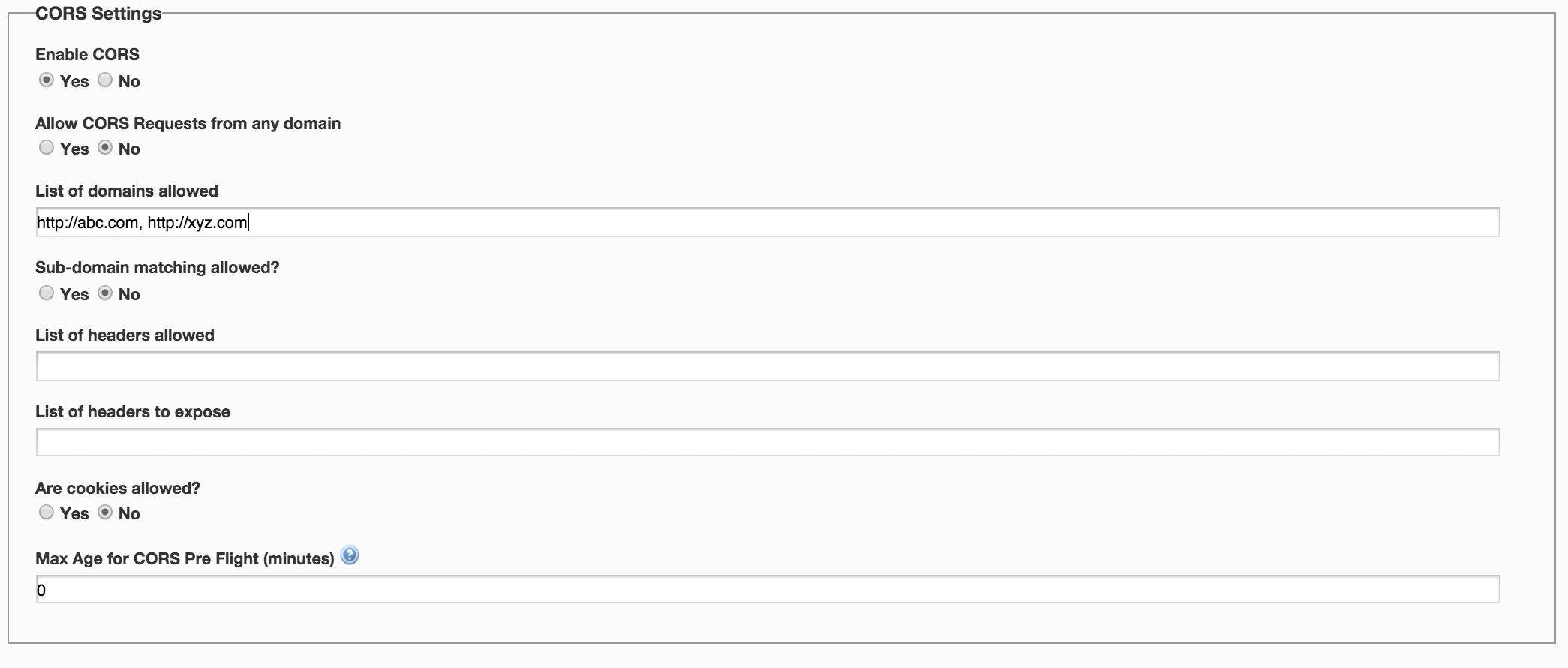
- If Allow requests from any domain is set to No on the Dashboard then:
- The API administrator can specify a comma separated "List of domains allowed". The requests made from domains that are not in the list are denied.
- To allow for more flexibility, API administrator can also select if "Sub-domain matching allowed" is Yes. By default, exact domain matching process is followed.
- In case of an exact domain match, for e.g. if http://abc.com, is specified in the “List of domains allowed”, only requests for http://abc.com are allowed.
- In case of a sub-domain match, for example, if http://abc.com is specified in the “List of domains allowed” on the Dashboard, requests coming from http://abc.com, http://xyz.abc.com and http://xxx.abc.com are accepted as valid and allowed through
- Note that in either of the above cases, http://abc.com, https://abc.com, and http://abc.com:8080 are not considered identical and are never matched
- CORS specification does not allow any custom header to be processed by the browser client application except if the server explicitly white-lists those headers via Access-Control-Expose-Headers. With the "List of headers to expose" field, API administrator can white-list the headers that Traffic Manager will add to Access-Control-Expose-Header in the response.
- API administrator can specify a comma separated "List of headers allowed". These are used to validate against values in Access-Control-Request_Header and determine if the request can be allowed through or not. If allowed, corresponding headers are added to Access-Control-Allow-Header back in the response. If this field is left empty, any incoming header is allowed – this is to maintain backward compatibility
- API administrator can specify whether cookies are allowed for the CORS requests or not. By default, cookies are not allowed. If cookies are allowed, Access-Control-Allow-Credentials is set to true on the preflight response and CORS response.
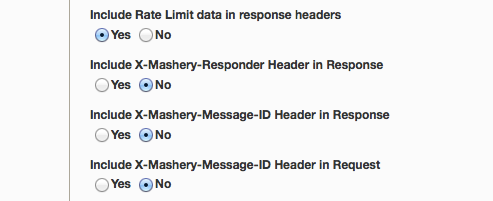
- To facilitate debugging scenarios for CORS request and response, any selected Mashery specific debug headers are white-listed via Access-Control-Expose-Headers so that the client application can process the response appropriately. Specifically if Include X-Mashery-Responder Header in Response, and Include X-Mashery-Message-ID Header in Response are selected on the end-point settings in the dashboard, these will be added to Access-Control-Expose-Headers list
- Even in the case of error responses, CORS specific headers are added in the response. This allows the client application to read and process the right error message
- Even if pre-flight request fails, it is returned with a 200 code but with the right error message This will ensure that the client application can process and display the appropriate error message on the browser which facilitates better debugging.
Rate limit consumption via debug headers
We launched a useful little feature recently that allows monitoring of rate limit consumption. This is a feature that needs to be be toggled on via a UI option to be available. When this feature is toggled on, all responses returned from that end-point will automatically include a bunch of Mashery generated headers that display information such as allotted QPS, allotted quota, current QPS, current quota as well as time duration left to quota reset. Useful for e.g. if a developer runs out of allotted daily quota and needs to know when the next call can be made against that end-point.
For e.g. with this option enabled, if a developer is making a call using a package key for a package plan that has method level limits specified, below are some headers that would be included into the response by Mashery
X-Plan-QPS-Allotted
X-Plan-QPS-Current
X-PlanMethod-QPS-Allotted
X-PlanMethod-QPS-Current
X-Plan-Quota-Allotted
X-Plan-Quota-Current
X-PlanMethod-Quota-Allotted
X-PlanMethod-Quota-Current
Here’s the screenshot of where you would enable this option via Endpoint -> Properties page ( Include rate limit data in response headers)
New Feature: Enhanced Cache Reporting and API Distribution Network
We are pleased to announce the general availability of enhanced Cache Reporting, the latest addition to the Reporting & Analytics provided within the API administration dashboard.
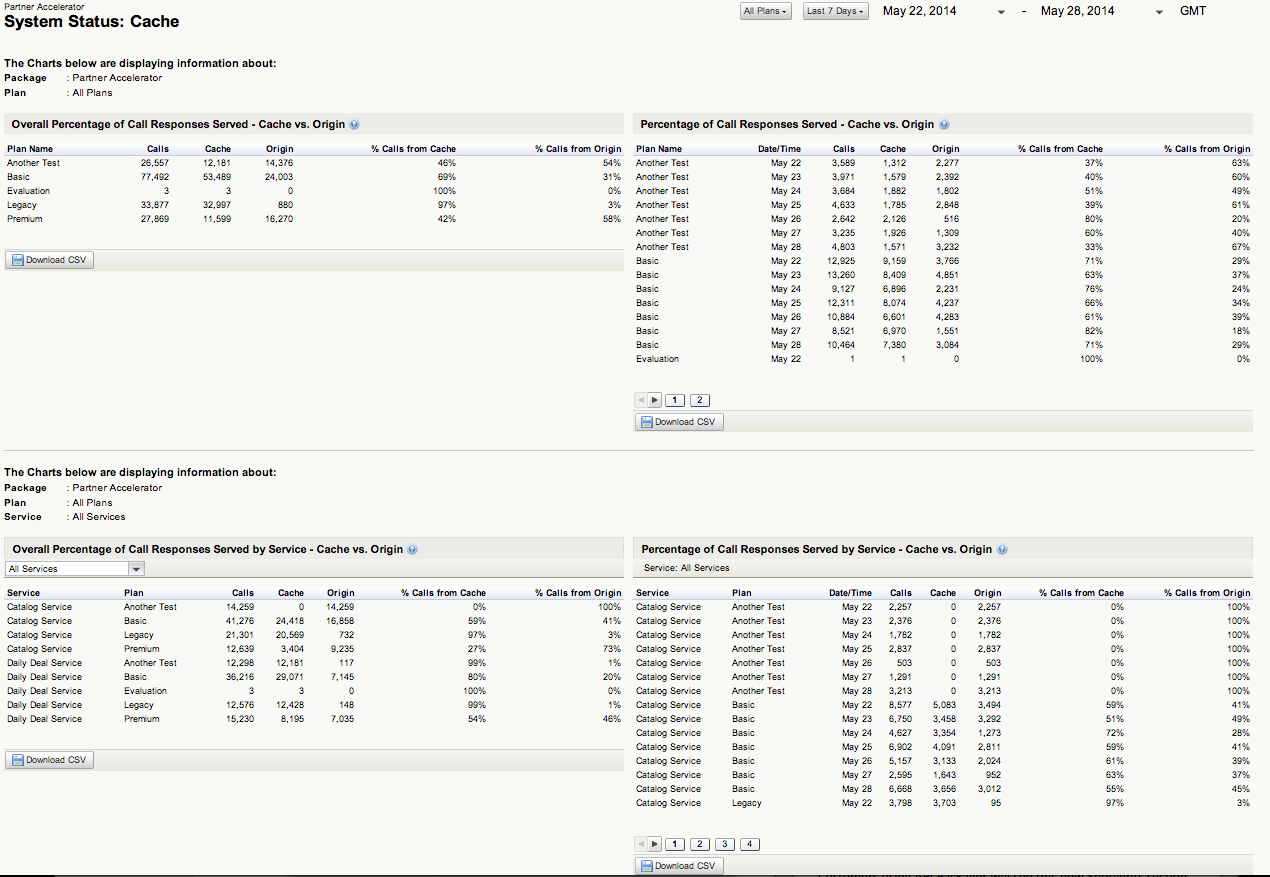
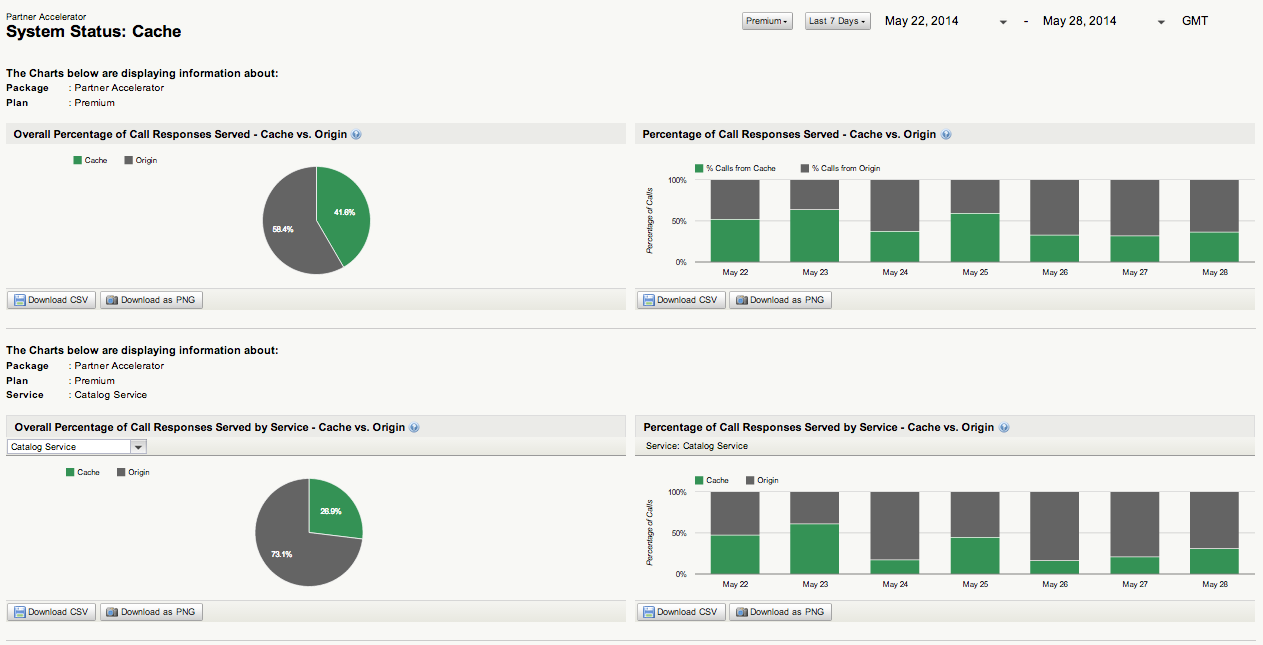
API administrators can now drill-down deep into their API programs and visualize the percentage of API responses that are being delivered from the Mashery cache feature or from their backend infrastructures.
Now, API administrators can proactively identify opportunities to unload non-transactional API traffic from consuming their backend capacity and instead leverage TIBCO Mashery’s globally distributed API distribution network. Customers delivering static data or rich-media content like videos, music, articles, etc…, who have optimally configured their use of the Mashery cache feature would see improvements to their API response times and, for any mobile-deployed products, a seemingly “faster” end-user application experience as data is transferred in less time.
The new reports provide a "birds-eye view" across Packages, Plans, API’s, Endpoints, Methods and developers. Each drill-down perspective contains a pair of reports for an overall assessment and a time-trended assessment of how the Mashery cache feature is being utilized. A key benefit of this deep visibility into cache utilization is the potential for our customers to influence internal discussions on how to improve the backend infrastructure with respect to the indicated traffic trends for APIs, endpoints, and methods.
When filtered, the report data tables transition smoothly to become an interactive data visualization for further inspection and insight generation.
The new reports are available for all customers who have the cache feature enabled and can be found within the Reports tab of the Administration dashboard at the following location: For a selected Package or Service > System Status > Cache.
Please see the screenshots below depicting this exciting new feature in action!
OpenSSL Exploit - SSL/TLS MITM vulnerability (CVE-2014-0224)
OpenSSL has released a new exploit notification (CVE-2014-0224), and as with all such exploits, Mashery is working to identify and patch any systems that might be subject to this exploit.
Unlike the previous HeartBleed exploits, we believe this vulnerability did not expose any customer certificate or private key information to an attacker. Whereas, with HeartBleed, customers were required to rotate out their Certificates and generate them with new Private Keys, in this case there is no action needed on the part of Mashery Customers.
We will be providing updates as more information becomes available on this or other security related topics.
Please don't hesitate to contact us via support@mashery.com or via the self service portal (mashery.com/selfservice) should you have any further questions.
Best, Scott
================================
Scott Farnsworth
Director, Technical Services | Mashery, Inc.
Cache optimizations with If-Modified-Since
We are excited to announce that with last night’s release, Mashery has included additional caching optimizations around handling If-Modified-Since header. This HTTP header can be quite useful to improve response times and reduce traffic bandwidth between client applications and your API back-end systems. The way If-Modified-Since header works is very simple. It simply allows any system that honors this header to evaluate if content has been modified since the date specified in the request. If content has not been modified since the date, the system responds back with “304 Not Modified” without sending back the entire payload. This way client applications can reliably use local caches to fulfill responses, speed up response times and avoid unnecessary response payloads getting downloaded from API back-end systems
To understand how this works and to benefit from this feature, you must first enable Mashery cache for the API end-point.
If an application sends a request with If-Modified-Since header against that end-point, Traffic Manager will first check if a valid response can be delivered from cache. If Mashery cache has a valid response, Traffic Manager will evaluate if the cached response needs to be revalidated against API back-end system based on additional directives such as “max-age”, “s-maxage”, "must-revalidate”. If revalidation is not called for, Traffic Manager will return back with a “304 Not Modified” response avoiding request / response roundtrip to the API back-end system. Even if revalidation is called for, Traffic Manager performs additional optimizations and converts the request to a conditional request to minimize traffic bandwidth to your API back-end system. If the API back-end system responds back with “304 Not Modified” in this case, Traffic Manager will deliver the valid response from Mashery cache. If the API back-end system responds back with a “200 OK”, response is delivered as usual to the client application and updated in cache.
New Feature: Expanded Cache reports
Mashery is pleased to announce the release of an new expanded set of reports that enables our customers to enjoy new levels of visibility into the API performance benefits provided by our caching feature.
Now, API administrators can drill-down into their technical asset hierarchy and visualize the percentage of traffic that is delivering responses from Mashery's Cache feature or from their backend technical infrastructure. Once filtered, the data table transitions to an interactive data visualization for further investigation and insight generation.
Cache utilization reports are available for all customers and can be found within the Reports tab of the Administration dashboard as follows:
For a selected Package or Service > System Status > Cache
Please see the screenshots below depicting this exciting new feature:


Heartbleed update 4/15/14
It has been a week since the initial reports of CVE-2014-0160, aka the Heartbleed exploit. Over this time we have been working closely with our customers to assist those who might have been exposed to this vulnerability in performing their own risk assessments based on their knowledge of their own systems and the information that we have provided. The purpose of this coordinated investigation is to allow customers to determine their level of risk and execute any required mitigation steps.
For Mashery, this has meant reviewing our infrastructure and connection points with customers to provide that all appropriate systems have been patched and any necessary certificates and credentials have been rotated as security best practices demand. We have sent out multiple communications directly to customers as they relate to specific threat vectors and continue to work with them to install new customer certificates as they come in.
The task of evaluating the risk not only to Mashery but also to our customers has been one that we have not taken lightly. We will continue to stay on top of this issue and message out as appropriate. Please contact us at support@mashery.com should you have any questions or feedback about this process.
Heartbleed Update
While the actual threat window has been closed, we have been working actively with our customers to rotate SSL certificates. We are also continuing to follow through with assessing any additional risks and remediation steps as necessary.
As a reminder, if you are deployed on the Mashery Enterprise network and have not already done so, please open a support case to begin the process of swapping out your SSL certificates. If you have questions or concerns or are not sure if you are using our Enterprise network, please contact us at support@mashery.com
Heartbleed Exploit Security Update
As you are probably aware, OpenSSL released a security advisory yesterday, April 7th, regarding a serious vulnerability nicknamed “Heartbleed”, which impacted a large number of Internet applications and services. The vulnerability allowed an attacker to steal private certificate keys or even gain access to data in memory of a vulnerable SSL server. Mashery, along with its service providers, has addressed this vulnerability and believes it has been resolved.
Prior to resolution, some Mashery customers may have been affected by this vulnerability though there is no log information associated with this exploit that allows Mashery to determine whether any systems were compromised. Customers exposed to the vulnerability included only those on the Mashery Enterprise network utilizing SSL certs to enforce secure communication between their consumers and Mashery SaaS systems. API traffic for Customers on Mashery's Premium Network and API traffic managed via Mashery Local were not exposed to the threat.
Mashery’s Enterprise network utilizes Amazon Web Services, which incorporates Elastic Load Balancers (ELBs) in traffic management. Amazon has issued statements today containing information on the vulnerabilities with ELBs as well as other Amazon offerings along with resolution information. According to their release, all AWS regions utilizing ELBs have been patched. Mashery is continuing to monitor any additional information released by Amazon and additional, related threats.
If you are using Mashery’s Enterprise SaaS edition with SSL transport on API traffic (SSL on the Mashery developer portal is not in scope for this vulnerability), we recommend that you replace your SSL certificate. To begin this process, please open a support ticket with Mashery via self service portal (mashery.com/selfservice) or by emailing support@mashery.com and our support group will walk you through the process.
We at Mashery continue to take security very seriously and are taking all measures possible to address this. Mashery continues to evaluate this vulnerability to determine if any additional systems were at risk during the vulnerability period. Mashery will provide any updates as they are available. Thank you for your patience on this issue. As always, please feel free to reach out to us if you have any additional questions or concerns.